KUKA shows that 3D printing offers significant advantages for the creation of modern industrial robotics.
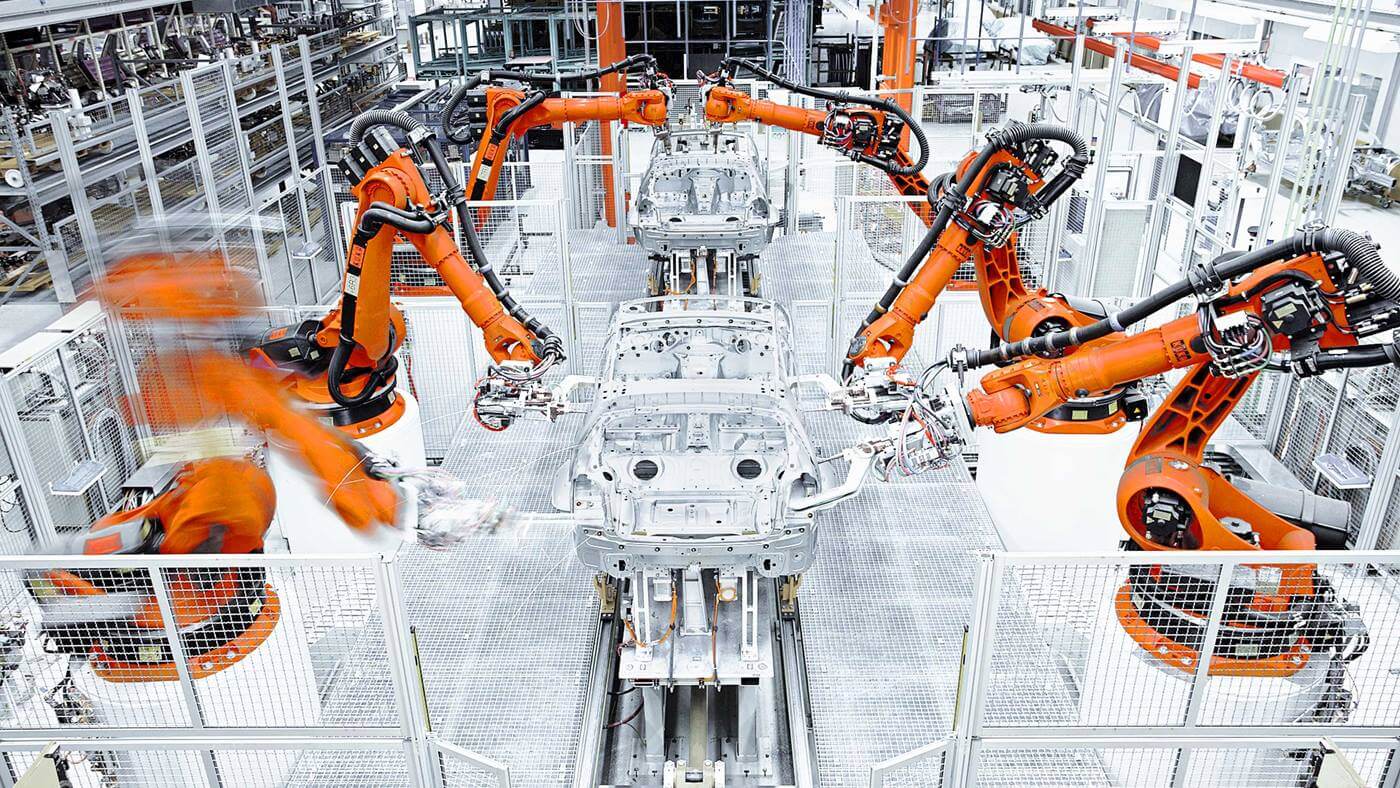
Driving the smart factories of the 21st century, industrial manufacturing industries are increasingly turning toward automated solutions. Robotics are being employed to ease the burden of lifting or transporting heavy loads.
KUKA, the Chinese-German industrial manufacturing company, creates specialist robotics by using 3D printing technologies.
In collaboration with MakerBot 3D printers, KUKA develops robotic arms which are used across a variety of industries.
The advantage of using 3D printed components is that the weight of the robot can be minimized. At the same time, the company has been able to reduce the number of parts used to assemble a robotic arm.
The company currently employs 14,000 members of staff worldwide. The robotic arms are available in different sizes and at various payload capacities.
However, KUKA robotics aren’t just built to automate processes. Instead, the company’s robotic systems have been created to make the working environment safer for people.
The six-axis industrial robots provide the reactivity and flexibility of a human with a payload capacity from 3kg to over 1 ton.
“We’re working on robotics, on solutions and automation for nearly every industrial area – for aerospace, electronics, general industries,” explains Otmar Honsberg, head of application engineering at KUKA.
Robots by KUKA during automobile manufacture. (Image: KUKA)
Human-robot collaboration made possible with KUKA
The company works with MakerBot fairly early during the engineering process. It supplies data for components to be 3D printed at the same time as it begins sourcing the metal components.
“Because we can do that development stage with one-to-one scale printed components. By the time we have actual aluminium or metal parts, we have already made a number of revisions,” adds Soeren Papsdorf, head of manufacturing engineering at KUKA.
Using just one 3D printer, the company printed 7,000 hours in 2016 at a success rate of 92%.
“To us, it’s very important that a printer is reliable,” says Thomas Schmidberger, applications engineer at the company. “3D printing is very important because every application is different and everything is customized.”
In addition, KUKA uses the 3D models to create the assembly process for fixtures and other parts.
By using additive manufacturing, the company is also able to create application tools in a shorter amount of time. In return, clients are receiving their robotics faster.
“I think human-robot collaboration is the future of robotics. Human-robot collaboration allows you to combine the advantages of a robot with the advantages of a human being. Seeing, feeling, being able to react quickly,” concludes Papsdorf.
Website: LINK